Published date:

Phishing is the most common method of cyber attack in Northern Ireland today. So what is it?
Phishing is when attackers attempt to get unsuspecting users to do 'the wrong thing', such as clicking a bad link that will download malicious software or direct them to a website that requires them to enter personal details.
Research has found that 91% of all cyber attacks start with a phishing email and according to Symantec Internet Security 1 in every 1,846 emails is a phishing email. To put that into perspective, there were 281 billion emails sent and received every day in 2018 and it is expected into increase to 347 billion by 2022 (Statista).
Phishing can be conducted via several platforms, text message, social media, or by phone, but the term 'phishing' is mainly used to describe attacks that arrive via an email. Phishing emails can be sent directly to a high volume of users, and can get easily lost within a busy Inbox. Attackers can use this email to install malicious software (malware), to render a system unusable (Denial of Service), to obtain personal details or to steal intellectual property and money.
Phishing emails can hit an organisation of any size and type. An attack may be part of a mass campaign where the attacker is just looking to collect passwords, personal details or make some easy money, or it could be the first step in a targeted attack against your company, where the aim is to steal sensitive data. In a targeted campaign, the attacker may use information that they already know about your employees or company to make their messages even more authentic looking. This approach is more commonly known as spear phishing.
Despite the attackers best efforts there may be tell-tale signs that indicate that the email isn’t genuine.
Check the domain where the email was sent from (the name after the @ symbol). Does the domain name match the organisations name? No legitimate organisation will send an email from a public email domain (@hotmail.com, @gmail.com). Look at the full email address and not just the sender name.
Is the email poorly written? Poor spelling or grammar can often give away the legitimacy of an email. Many attacks come from foreign countries where English isn’t the first language.
What is the overall quality of the email? Does the email look legitimate and is it what you would expect from the organisation that it is supposed to come from?
Does the email contain suspicious attachments or links? In a suspicious email attachments and links are known as the ‘payload’. The attachment while it may look genuine contains Malware designed to infect your system and perform any number of commands. While the link will direct you to another website where you may be asked to enter sensitive information about yourself or your company.
Is there an urgency in the email? Attackers don’t want you to have the time to think about the content of the email so they will write it with a sense of urgency asking you to ‘act now’ before it’s too late.
Does it sound too good to be true? Many attackers try to convince you that there is a benefit for you if you open an attachment or a link. If an email tells you that you’ve won a prize and that you have to click on a link to claim it, think before you act, did you enter a competition?
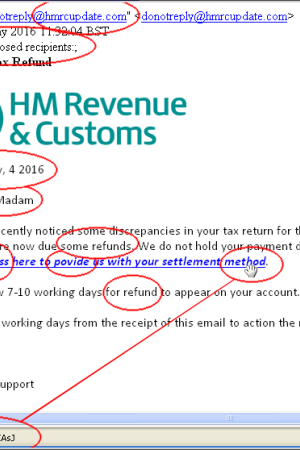
From the sample email below we can see several areas of concern that we covered above. The email is from a non-government domain, the recipient has not been identified and has been addressed as ‘Sir | Madam’. There is no month in the date, there are examples of poor English ‘Press Here’, ‘povide’ instead of provide, ‘for refund’. When you hover over the link you can see that it directs you to a non HMRC address. Lastly, the email contains the urgency element as it sets out a deadline that you must reply by.
Through education, we can prevent phishing attacks from being successful. It is important for SME’s to provide advice and guidance to all staff in regards to how to identify a suspicious email, text message or telephone call.
For further information is available from the National Cyber Security Centre's Small Business Guide to help SME's to protect themselves from the most common cyber attacks.